Top Tip: Managing PGP in Globalscape EFT
By Ye-Kwan Pang | Mar 14, 2022 |
One of the top questions customers ask us is how to manage PGP in Globalscape EFT. To answer this, our EFT expert Richard Auger takes us through a step-by-step process of setting up a transfer.
What is PGP?
Firstly, what is PGP? PGP, or Pretty Good Privacy, is a tool for encrypting documents, working on the PKI (public key infrastructure) principles.
It’s used to provide encryption while a file is at rest and also in transit; I provide you with my public key and you can encrypt a file with it to send to me.
PGP is still heavily used despite the fact that the majority of transfers are sent over encrypted protocols (SFTP/FTPS/HTTPS) and many managed file transfer systems have built in functionality to encrypt whole directories.
For example, a number of banks require PGP encryption as an extra safeguard if a file goes to the wrong client – an inability to decrypt a file due to the wrong key would prevent financial data being misdirected.
How to use PGP in EFT?
In fact, there are two ways – firstly through event rules, secondly via the Advanced Workflow Engine. In this article, we will look at use of PGP in event rules.
PGP keys are now stored at the site level, rather than at the server level. This gives you some flexibility to keep the keys tidy by having different rules for different sites. Of course, it can also be a problem if you wanted to use one key across all sites, however, that would be quite a rare circumstance. PGP keys are grouped together in a PGP keyring; to manage this keyring, go to the tools menu and select ‘manage OpenPGP keys’, then simply select the site on your EFT server that you want to work with.
We will start by creating a new key pair (private and public key) by clicking the ‘New’ button. Click next when prompted, then you have the opportunity to select some configuration options.
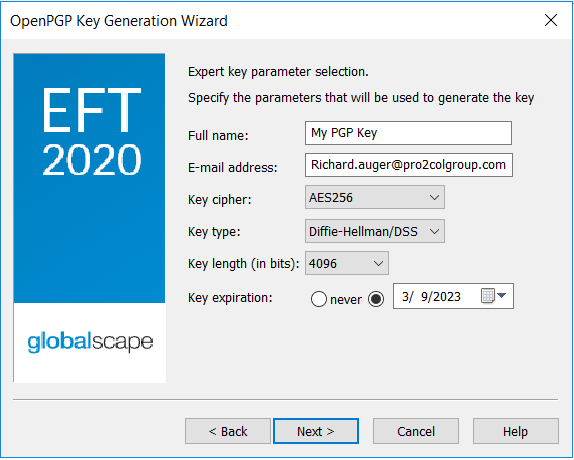
The key name should represent how you want to refer to the key; the email address should be a real address that notifications can be sent to. I would recommend that you use the AES256 cipher to encrypt files with, but as far as key type goes (DH/DSS or RSA), this really comes down to what your trading partners can work with. Remember that the key length should ideally be the largest that you can work with – longer keys provide more security and as long as you have a good size, DH/DSS and RSA are to all intents and purposes equally secure.
Finally, be sure to expire your keys regularly for extra security. You will be prompted for a passphrase to protect the key with – be sure to record this as you cannot reset it later.
Because I want to encrypt and send files to a trading partner, I’ve imported their public key, as well as creating my own key pair.
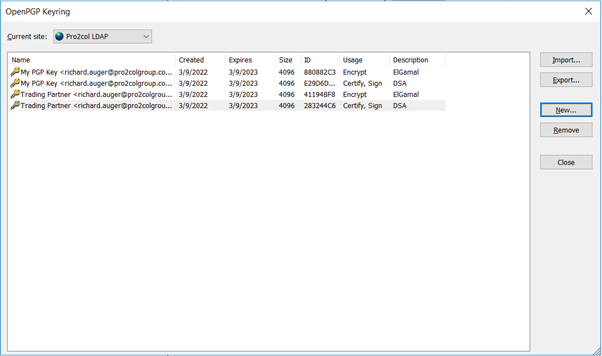
As well as simply encrypting a file, we can also use our own private key to sign the file to prove that we are the sender (public keys can be shared to many people, but private keys always stay with the owner), so I will need to export my public key and send it to the trading partner (the key with usage=encrypt).
Now I can create a rule to encrypt a file to send to my trading partner:
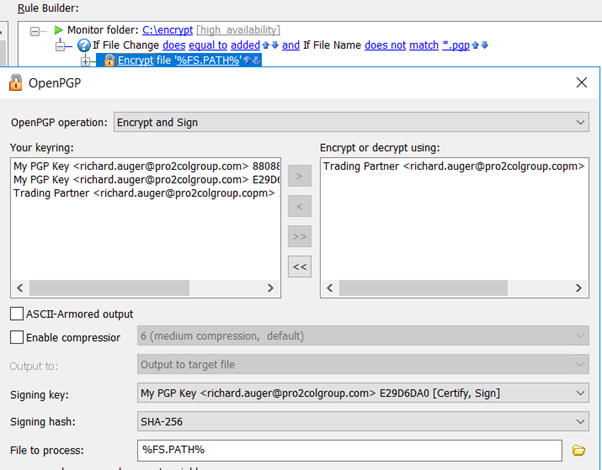
You’ll notice a few things going on here – first, my folder monitor has been told to ignore *.pgp files. This is so that I do not trigger the monitor to process the file again (during the encryption, the file will be renamed to have a .pgp extension). Next, I am using the trading partners public key to encrypt, but my private key to sign. Finally, although not shown here, even in the upload step I am using the ‘magic’ variable %FS.PATH% which will now contain the new filename with .pgp extension.
In the destination system, we can use Decrypt & Verify to ensure that the signature matches the sending signature, and decrypt the file:
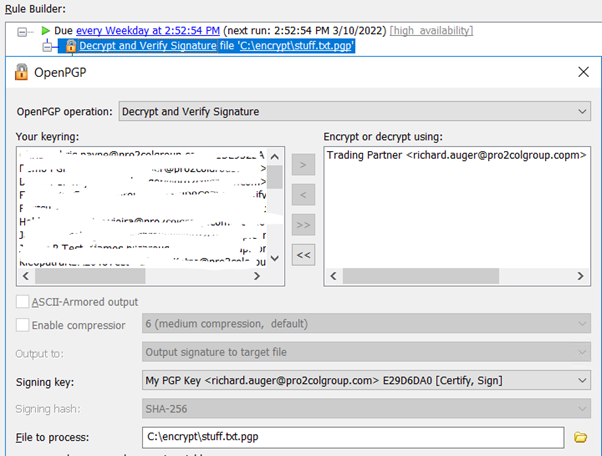
The important thing to remember is that the sender always encrypts a file with the recipients public key and signs it with their own private key; the recipient decrypts the file with their own private key and verifies the signature with the senders public key.
There you have it how to manage PGP in Globalscape EFT. We hope you found this helpful, but feel free to contact us if you have any further questions.

EFT Modules





