HIGH SECURITY MODULE (HSM)
Achieve or Exceed Industry, Government, and Corporate File Transfer Security Standards
With support for multiple security protocols and cryptographic ciphers, the High Security module (HSM) thoroughly protects data in transit. By enforcing the use of secure protocols, strong ciphers, encryption keys, and password policies, data transfers strictly follow all security guidelines.
With HSM security, you can enforce account access policy controls, expire passwords automatically on certain dates, and use AD, NTLM, LDAP, an ODBC-compatible database, or the built-in authentication manager in EFT.
Ongoing Standards Compliance
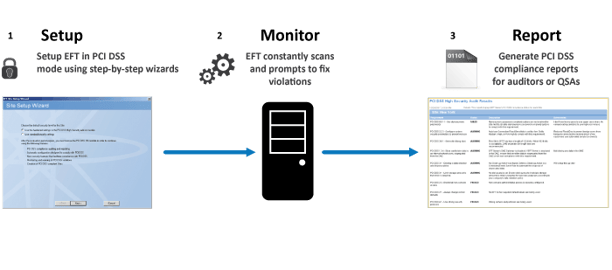
Securing sensitive company data requires continuous monitoring and validation of security policies and controls. Once enabled, the HSM is an ever-vigilant security tool that disallows low-security options, captures compensating controls, and generates reports for auditing the system’s compliance status.
The HSM actively monitors PCI DSS by alerting on non-compliance, identifying the cause of non-compliance, allowing reverting of security controls, implementing mitigation/workaround techniques. The Auditing and Reporting module (ARM) captures all of this activity in a fully relational database.
Protection of Data at Rest
Setup wizards provide administrators with an easy, step-by-step method for configuring a new high-security-enabled site, with each page describing the requirement and what you need to do to meet that requirement or to provide a compensating control (workaround).
The HSM, when used with the DMZ Gateway®, helps organizations comply with data storage requirements—including not storing data in the network DMZ—using repository encryption and securely sanitizing (wiping) deleted data so that it cannot be reconstituted.
KEY FEATURES
-
Minimise attack vector
-
Compliance with standards
-
Easy security configuration
-
Protection of data at rest
-
Protection of data in transit
-
Controlled access to data
-
Actively monitor PCI DSS compliance

